|
 |
 |
|
 Arooj Masood Arooj Masood |
 Tran Nam Phuong Tran Nam Phuong |
|
|
|
 |
 |
 |
|
| Vehicular Networks |
| Vehicular networks, also known as Vehicular Ad Hoc Networks (VANETs), are a type of wireless network that connects vehicles to each other and to the infrastructure around them. These networks enable communication between vehicles, as well as between vehicles and roadside infrastructure such as traffic lights, road signs, and sensors. |
| Vehicular networks can be categorized into two types: Vehicle-to-Vehicle (V2V) and Vehicle-to- Infrastructure (V2I). V2V communication allows vehicles to communicate with each other directly, while V2I communication involves vehicles communicating with infrastructure. |
| Vehicular networks use a variety of wireless communication technologies, including Dedicated Short Range Communications (DSRC), Cellular Vehicle-to-Everything (C-V2X), and Wi-Fi. These technologies allow vehicles to transmit and receive data in real-time, enabling a range of applications and services such as traffic management, collision avoidance, and infotainment. |
| For example, if a vehicle detects an obstacle in the road, it can transmit this information to other vehicles in the area, allowing them to take evasive action. Overall, vehicular networks have the potential to transform the way we travel, making our roads safer, more efficient, and more connected. |
|
|
|
| Intellectual Merits and Broader Impacts |
| (1) Vehicular edge computing |
| (2) Vehicular edge caching |
| (3)Vehicular cloud computing |
| (4)Security and privacy issues in vehicular cloud computing |
| (5) Broader Impact |
|
|
|
|
| (1) Vehicular edge computing |
| Vehicular networks can greatly benefit from edge computing, which involves processing and analyzing data at the edge of the network, closer to where the data is generated, rather than in a centralized data center. Edge computing can enhance the performance and efficiency of vehicular networks by enabling real-time data processing and reducing latency |
| In vehicular networks, edge computing can be used to support a range of applications and services. For example, edge computing can be used to process data from vehicle sensors and cameras in real-time, enabling applications such as collision detection and avoidance. Edge computing can also be used to support traffic management and optimization by processing data from traffic sensors and providing real-time traffic updates to drivers. |
|
|
|
|
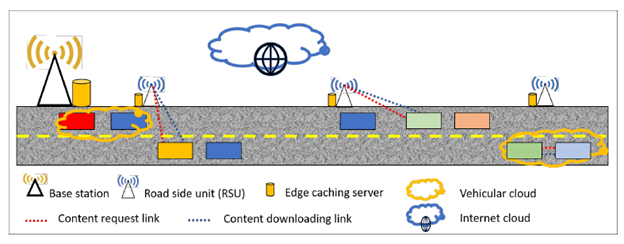
| (2) Vehicular edge caching |
| VEC, which utilizes the storage resources provided by the smart/autonomous vehicles and road-side edge servers, allows caching the popular contents at the edge of the VNs. Caching contents at the edge enables vehicles to retrieve requested contents in one transmission hop. The advantages of VEC is threefold. First, the latency for retrieving contents for latency sensitive vehicular applications can be greatly reduced and the duplicate transmissions from the remote content servers can be avoided. Second, as the data transmissions through the backhaul links are avoided, it can reduce congestion on the backhaul network. Third, it can leverage the network information collected by the mobile edge servers (MEC) (e.g., content preferences, contextual information, and social relationship) to improve caching efficiency in VEC systems. |
|
|
 |
|
|
|
|
| (3) Vehicular cloud computing |
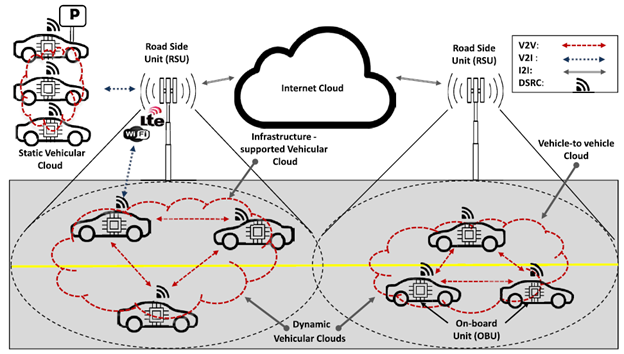
| Vehicular cloud computing (VCC) is an emerging technology that revolutionizes network service provisioning by incorporating the characteristics of vehicular networks and cloud computing for on-demand self-services. VCC allows a group of vehicular network entities, such as vehicles and RSUs, within a certain range (approximately 300m) to autonomously share on-board resources and self-organize to form a cloud of large computing facilities. VCC manages on-board computing, communication, sensing, and storage resources to balance resource limitations and service requirements.
|
|
|
 |
|
|
|
|
| (4) Security and privacy issues in vehicular cloud computing |
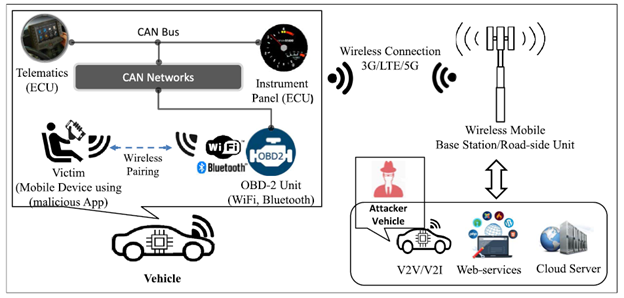
| VCC is considered the key enabling technology that provides value added services to drivers and passengers. However, the security and privacy of VCC is a critical requirement because legitimate users and attackers have equal privileges to share the same physical infrastructure]. In most scenarios, attackers aim to alter the confidentiality, integrity, and availability of information on the cloud. The classic security and privacy problems related to standalone vehicular networks and mobile cloud computing environment are unchanged even if VCC technology merges both the vehicular and mobile cloud computing environments. However, there are several security and privacy challenges in VCC because of the autonomous and dynamic nature of vehicular clouds (VCs). A vehicle can dynamically join or leave the cloud at any moment, and there is no means of differentiating between a trusted vehicular resource and an attacker’s resource. An attacker can masquerade as a legitimate cloud user and store malicious information on the cloud. Because VCC is based on the aggregation of shared resources, attackers can utilize system loopholes to obtain confidential information related to the vehicle or sensitive information. These attackers can tamper with the integrity of such information. An adversary may attempt to launch a denial-of-service (DoS) attack, such as jamming, to disrupt continuous cloud services or may attempt to inject malware to infect the credibility of the information on the cloud.
|
|
|
 |
|
|
|
|
| (4) Broader Impact |
| The project is expected to pave the way for DTN-based Multi-Modal Multilink Bundle Protocol (hereinafter referred to as Space Communication Technology) that can be used to develop mutually beneficial space and strengthen domestic space technology capabilities. The developed space communication technology can transmit control signals to probes/landers, receive lunar data, etc., and develop communication modules using domestic satellites and provide high-capacity satellite services through space communication. |
|
|
|
 |
|
 |
 |
 |
|
 |
A. Masood, D. S Lakew, and S. Cho,
"Security and Privacy Challenges in Connected Vehicular Cloud Computing,"
to appear in IEEE Communications Surveys and Tutorials, vol. 22, no. 4, pp. 2725-2764, July 2020.
[PDF]
[IEEE Xplore]
|
 |
A. Masood, DQ Tuan, DS Lakew, N. -N Dao, and S. Cho,
"A Review on AI-Enable Content Caching in Vehicular Edge Caching and Networks,"
to appear in in Proc. of IEEE International Conference on Artificial Intelligence in Information and Communication (ICAIIC), Bali, Indonesia, February, 2023.
[PDF]
|
|
|
|
 |
|
|
|
|
|